March 2019’s Most Wanted Malware: Cryptomining Still Dominates Despite Coinhive Closure
Check Point’s latest Global Threat Index sees cryptominers continuing to lead the top malware list despite Coinhive ceasing operation
In March 2019, Coinhive dropped from the top position of the global threat index for the first time since December 2017. Despite closing its services on the 8th March, it still held 6th place in the list. Cryptoloot now leads the top malware list for the first time, and cryptominers continue to dominate amongst the most prevalent malware aimed at organizations globally.
Despite its closure, the Coinhive JavaScript code is still in place on many websites. No mining is taking place, but if the value of Monero increases significantly, it is possible that Coinhive may come back to life. Another possibility is that we may see other cryptominers increasing their activity in Coinhive’s absence. Instead of taking aim at websites, though, which is bringing in limited gains since cryptocurrency values began to fall across the board after the highs of 2018, they may increasingly take aim at enterprises’ Cloud environments.
The built-in scalability of cloud environments allows mining to take place at far higher volumes. Check Point’s research team have begun to see organizations being asked to pay hundreds of thousands of dollars to their Cloud vendors for the compute resources used by rogue cryptominers. This is a stark warning for organizations to secure their cloud environments from malware.
March 2019’s Top 10 ‘Most Wanted’:
*The arrows relate to the change in rank compared to the previous month.
- ↑ Cryptoloot – Crypto-Miner, using the victim’s CPU or GPU power and existing resources for crypto mining – adding transactions to the blockchain and releasing new currency. It is a competitor to Coinhive, trying to pull the rug under it by asking a smaller percentage of revenue from websites.
- ↑ Emotet – Advanced, self-propagate and modular Trojan. Emotet once used to employ as a banking Trojan, and recently is used as a distributer to other malware or malicious campaigns. It uses multiple methods for maintaining persistence and evasion techniques to avoid detection. In addition, it can be spread through phishing spam emails containing malicious attachments or links.
- ↑ XMRig– Open-source CPU mining software used for the mining process of the Monero cryptocurrency, and first seen in-the-wild on May 2017.
- ↑ Dorkbot- IRC-based Worm designed to allow remote code execution by its operator, as well as the download of additional malware to the infected system.
- ↔ Jsecoin – JavaScript miner that can be embedded in websites. With JSEcoin, you can run the miner directly in your browser in exchange for an ad-free experience, in-game currency and other incentives.
- ↓ Coinhive – Crypto Miner designed to perform online mining of Monero cryptocurrency when a user visits a web page without the user’s knowledge or approval the profits with the user. The implanted JavaScript uses great computational resources of the end users to mine coins and might crash the system.
- ↑ Ramnit– Banking Trojan that steals banking credentials, FTP passwords, session cookies and personal data.
- ↓ Nivdort –Multipurpose bot, also known as Bayrob, that is used to collect passwords, modify system settings and download additional malware. It is usually spread via spam emails with the recipient address encoded in the binary, thus making each file unique.
- ↑ Lokibot- Info Stealer distributed mainly by phishing emails, and is used to steal various data such as email credentials, as well as passwords to CryptoCoin wallets and FTP servers.
- ↑ Mirai- Famous Internet-of-Things (IoT) malware that tracks vulnerable IoT devices, such as web cameras, modems and routers, and turns them into bots. The botnet is used by its operators to conduct massive Distribute Denial of Service (DDoS).
This month Hiddad is the most prevalent Mobile malware, replacing Lotoor at first place in the top mobile malware list. Triada remains in third place.
March’s Top 3 ‘Most Wanted’ Mobile Malware:
- Hiddad – Android malware which repackages legitimate apps and then released them to a third-party store. Its main function is displaying ads, however it is also able to gain access to key security details built into the OS, allowing an attacker to obtain sensitive user data.
- Lotoor– Hack tool that exploits vulnerabilities on Android operating system in order to gain root privileges on compromised mobile devices.
- Triada – Modular Backdoor for Android which grants super user privileges to downloaded malware, as helps it to get embedded into system processes. Triada has also been seen spoofing URLs loaded in the browser.
Check Point’s researchers also analyzed the most exploited cyber vulnerabilities. CVE-2017-7269 is still leading the top exploited vulnerabilities with a 44% global impact. Web Server Exposed Git Repository Information Disclosure and is in second place, with OpenSSL TLS DTLS Heartbeat Information Disclosure in third, both impacting 40% of organizations worldwide.
March’s Top 3 ‘Most Exploited’ vulnerabilities:
- ↔ Microsoft IIS WebDAV ScStoragePathFromUrl Buffer Overflow (CVE-2017-7269) – By sending a crafted request over a network to Microsoft Windows Server 2003 R2 through Microsoft Internet Information Services 6.0, a remote attacker could execute arbitrary code or cause a denial of service conditions on the target server. That is mainly due to a buffer overflow vulnerability resulted by improper validation of a long header in HTTP request.
- ↑ Web Server Exposed Git Repository Information Disclosure– An information disclosure vulnerability has been reported in Git Repository. Successful exploitation of this vulnerability could allow an unintentional disclosure of account information.
- ↑ OpenSSL TLS DTLS Heartbeat Information Disclosure (CVE-2014-0160; CVE-2014-0346) – An information disclosure vulnerability exists in OpenSSL. The vulnerability is due to an error when handling TLS/DTLS heartbeat packets. An attacker can leverage this vulnerability to disclose memory contents of a connected client or server.
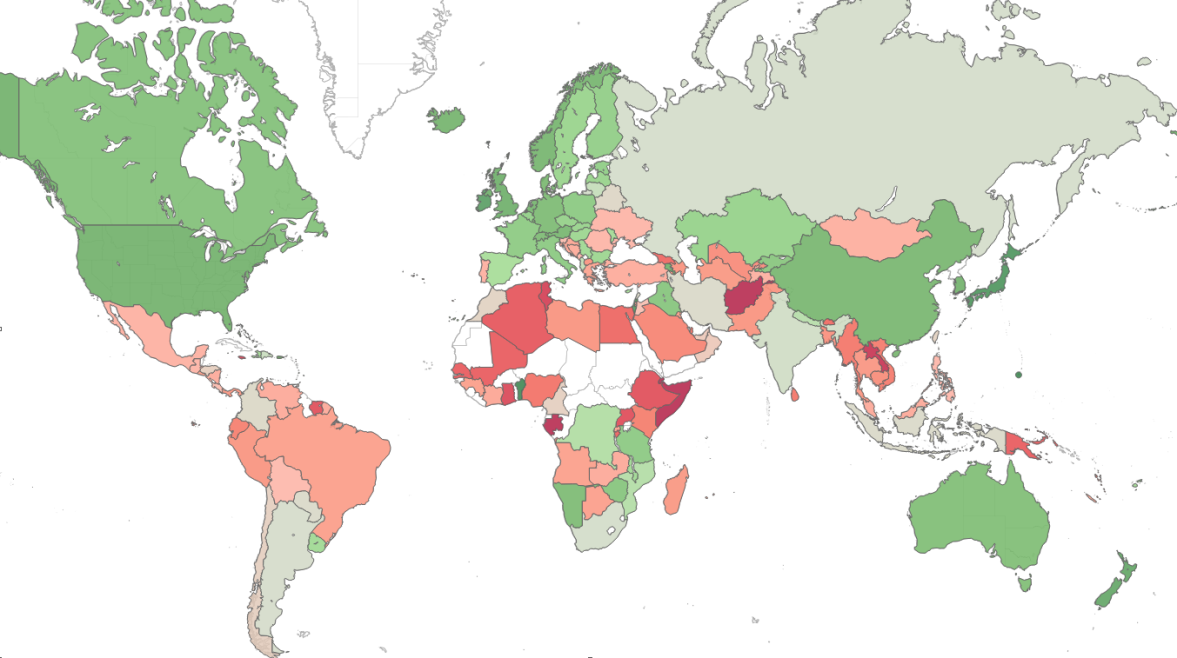
The map below displays the risk index globally (green – low risk, red- high risk, grey – insufficient data), demonstrating the main risk areas and malware hot-spots around the world.