Dragonblood Vulnerability: Is your WiFi secure?
It’s Game of Thrones season! And anything to do with dragons remin... read more
Wi-Fi 6 is for Developers
Wi-Fi 6 is here, and it opens a new chapter in networking. With its enhanced connectivity, the way w... read more
A data breach also means a breach of customer trust
As a business owner, you might be aware of the fact that people only buy from businesses they know, ... read more
Department of Homeland Security issues security warning for VPN applications — Check Point VPNs not affected
On Friday April 12, The CERT Coordination Center (CERT/CC) with the US Department of Homeland Securi... read more
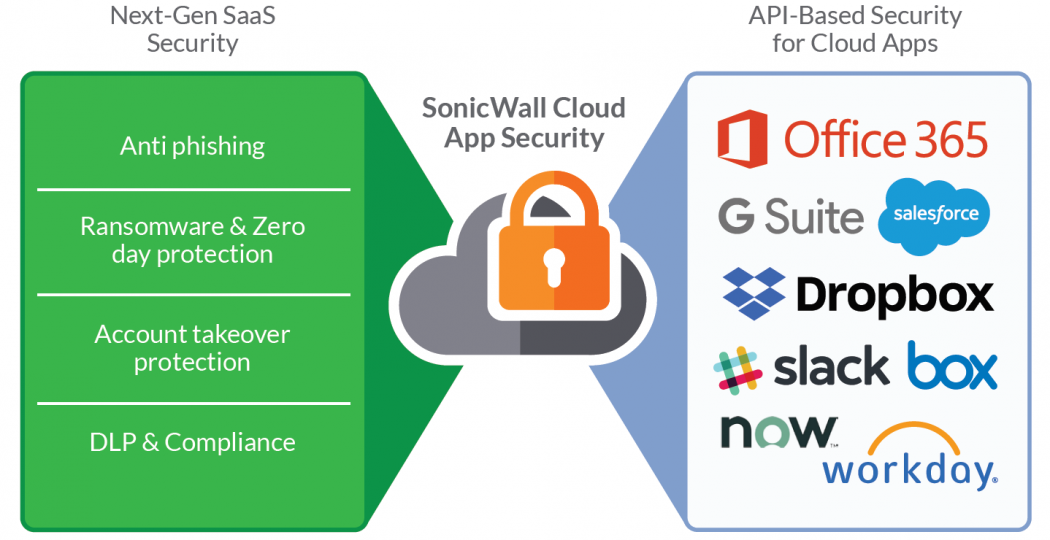
Comfortable as a Cloud with Cloud App Security
Whether for email, documents, storage, or something else, your business most likely needs (or will n... read more
ISPs Must Take the Wheel when Driving The IoT in Their Networks
From connected vehicles and vending machines to smart meters and wearables. The Internet of (connect... read more
7 Reasons to Adopt a Policy-Centric Approach to Security and IT Operations
What would it be worth to your business to be able to deploy application changes on the network in m... read more
Microsegmentation: look before you leap
Microsegmentation is trending among enterprises of all sizes. However, if you’re considering segment...... read more
March Firewall Madness
Spring is near and March Madness is here. March Firewall Madness that is! While much of the country ...... read more